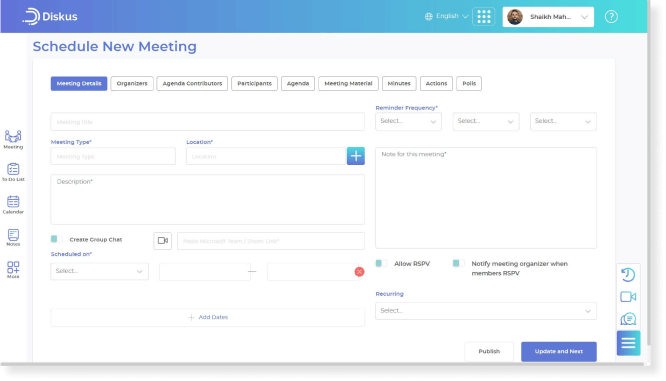
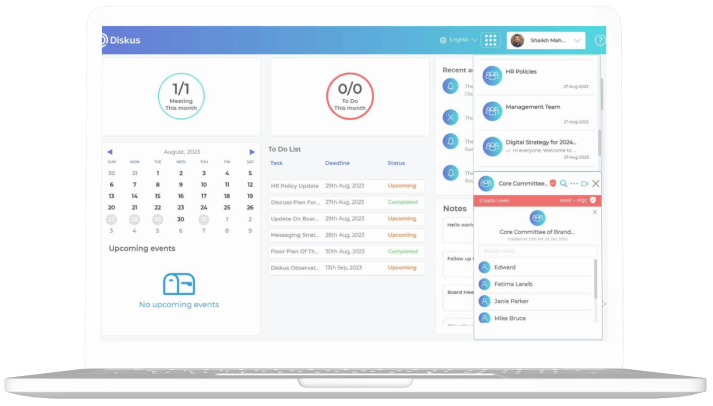
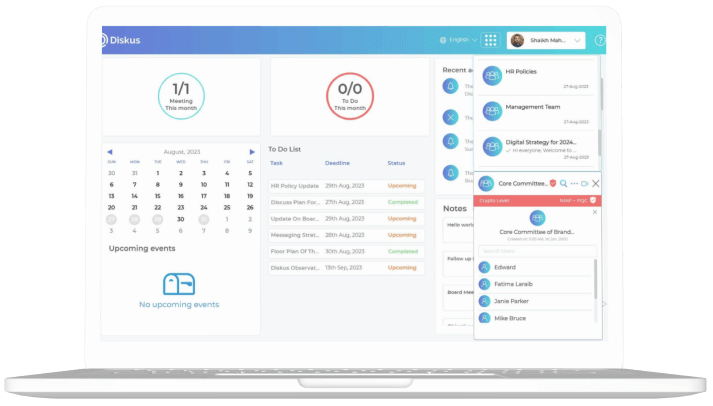
Security at Diskus
Diskus takes pride in its security and compliance standards. We are committed to providing our customers with a safe and secure platform that protects user's confidential information and data. We adhere to strict security standards, conduct frequent checks, and continuously monitor and audit to ensure the security of customer's data.